The cybersecurity problem is deeper than anyone wants to admit. Today, one of the most alarming cybersecurity concerns is the significant cost of a security breach. But considering abuses in the areas of cryptocurrency,1 artificial intelligence (AI),2 and ransomware,3 it is not an unfounded fear that the world will one day face a cybersecurity disaster on the scale of a natural disaster if a remedy to this emerging risk is not found.
Following the theoretical concepts discussed in the previous ISACA Journal articles, “Chaos to the Rescue” and “Against the Quantum Threat: Selective Compatibility,”4 it is time to recreate a conceptual machine to meet the many challenges of cybernetics. Cybernetics was first defined by Norbert Wiener as the study of control and communication in the animal and the machine.5 From this general definition, cybernetics can be further focused on the human-machine interaction in cybersecurity.6 It is the origin of computing.7
There is a need to design a new Turing machine, and the authors proposed a theoretical approach.8
The Turing Machine
Before imagining a theoretical new Turing machine, it is helpful to understand the existing, traditional Turing machine.9 Even today, computers continue to operate according to the rules of this conceptual machine designed nearly a century ago.
Attempting to enable machines to perform human tasks is nothing new. Consider Pascal’s calculator10 or Babbage’s machine.11 The creators of these machines had to adapt the technology in use at the time to make daily activities easier. Pascal’s machine was intended to make arithmetic calculations easier and faster, while Babbage’s machine enabled a tool to weave without the intervention of a human hand. However, the Turing machine is different. Its purpose is not to use existing technology to perform a task in an improved way. Rather, English mathematician and computer scientist Alan Turing’s aim was to create a conceptual machine with a mission to predict how a machine that does not yet exist should work. His machine essentially created IT from scratch. And it can be used for years to come in the design of new machines—even when the quantum computer emerges. So, the goal is by no means to reject the Turing machine, but rather to integrate it with a machine made more complex by the phenomenal advances in modern technology.
The New Turing Machine
The authors have formed five hypotheses, which constitute the cornerstone of their research:
- A baby born today does not need a name or a number to be authenticated by a computer.
- On a certain scale (e.g., micrometer, millisecond), it is impossible for two objects to be perfectly identical.
- A computer can protect users by protecting itself.
- To become more secure or even inviolable, information systems must obey a logic other than Boolean logic and obey laws different from the theory of compilation and Von Neumann’s architecture.12
- It is now possible, based on the four previous hypotheses, to design information systems with limited compatibility (i.e., it may become impossible for two machines to communicate with each other without some prior interaction).
The relevance of these assumptions should be considered—or even challenged—by disregarding any philosophical or economic implications of their application to the new cybernetics.
The hypothetical design of a new Turing machine can be based on these five fundamental assumptions. These five hypotheses, supported by certain advances in modern technology, introduce five possibilities. However, it is important to note that these five possibilities are not the only possibilities.
Careful consideration of these possibilities may help address not only current problems, but also the future threat of the quantum compiler in being able to decipher all the keys in use on the Internet. These five premises, associated with the new Turing machine, enable the creation of information systems wherein:
- Every user has a virtual alter ego (i.e., a set of interfaces that guarantees each action performed by the system truly originated from the authorized user)—This alter ego should not, in any way, replace the user in the virtual world. The virtual alter ego should be able to accompany the user and confirm that every action the user performs in the virtual world is carried out by the user and not by someone else or another machine (e.g., a computer or robot). Of course, this functionality can currently only be considered from the angle of technical feasibility. It is up to philosophers and jurists to consider the positive and negative impacts that could arise from using this new feature.
- The physical layer of the Open Systems Interconnection (OSI) model is no longer considered a passive layer limited to the passage of electric current; rather, it is an essential controlled gateway—The physical layer describes the electrical, logical, and physical characteristics of the system (i.e., all the components from the type of cable to the radio frequency link).13 Historically, this layer has been considered either the end of any system that initiates a computer transaction or the entry point for any system that receives and processes the transaction. The consensus is that it is no longer possible for humans to intervene to modify, secure, or stop an ongoing transaction.14 The processes of data circulation, encapsulation, and encryption have been performed by layers two to seven. At layer one, the electronic current simply needs to pass. There is a need only to submit to the capacities and performance of the frequency bandwidth of the channels used. A so-called colored bit algorithm has been designed so that once it has reached the implementation stage, it will be responsible for giving a whole new impetus to the first layer of the OSI model.15 In the new Turing machine, the behavior will not be the same because electron flows will no longer be passive; they will participate in message routing and encryption.
- Containment is considered the default state—This is the Achilles heel16 of existing information systems. As soon as a flaw is discovered in an operating system (OS) or application, all systems using the same OS or application automatically become vulnerable, regardless of their point of access. To avoid any negative impact, a patch must be produced as soon as possible. With the emergence of increasing zero-day threats and the erosion of traditional security perimeters, this issue is likely to lead to catastrophe because it can be difficult to immediately produce an adequate patch. To remedy this, one proposed approach is to make the operation of some computers strictly compatible with the operation of certain other computers. This measure aims to significantly slow down (or mitigate altogether) future threats that may occur due to the spread of malware through the most sensitive and well-protected information systems. For example, during the WannaCry attack, many hospitals in the United Kingdom were not able to access patients’ data.17 Default containment will prevent this rapid spread because it will be impossible for threats to penetrate elsewhere in the event that the correct update cannot be identified and executed immediately.
- The compiler supporting this new logic makes it possible to perform multicoding—It is common knowledge that it is possible to use number systems other than binary calculation. In everyday life, the decimal system (zero through nine) prevails. The founding fathers of cybernetics chose binary calculation (i.e., Boolean logic).18 But in recent years, new coding systems based on other numbering systems have emerged. Without entering into the world of qbits, there are two new types of coding to consider:
- A coding system that stems from storage on synthetic DNA–With four initial bits, this mode of coding information is quite revolutionary because it makes it possible to store high volumes of information in increasingly small spaces.19
- A coding system based on the colored bits (with eight initial bits)–By going from 16 (2^4) possible combinations with the traditional symbols 0 and 1 to 256 combinations (2^8), the proposed information system will possess exponentially increased coding capacity.20
- Objects (e.g., information systems, robots, consumer goods, medications) designed by humans are protected by certain mechanisms to prevent them from replication or counterfeit—There is an increasingly popular sentiment that because of technology, privacy is becoming a luxury that no one, regardless of level of wealth, can afford. The philosophical or ethical implications that such an assertion could have on the future of humanity are not yet wholly understood. However, consider a more basic consequence: the dangers to everyday life and the world economy that could result from the rise of proven falsification. Manufacturers of luxury products (e.g., wines, perfumes, clothing) and medications find themselves disarmed as counterfeiters discover new methods to circumvent controls. High volumes of falsified products, drugs without any therapeutic virtue, and, in some cases, real poisons are thrown away daily around the world.21 Some countries have even found a way to place themselves in a favorable position on the world economic scale. And what about the multiplication of cryptocurrencies and the hacking of the central banks of small countries by rogue totalitarian states, such as the case of the Bangladesh Central Bank hack?22 All this strengthens the quest to find a new way of designing information systems. It is possible to know that a bottle of wine or medicine has truly left the premises of its authentic manufacturer on a given day, at a given time. The packaging, the container, and the contents of the product are there to certify it. These contain unique microscopic traces (only detectable by information systems built specifically for the product designers, according to the second hypothesis) that protect them from any attempts at counterfeiting. This is why the proposed system will not only protect against privacy violations and identity theft, but also could help humanity avoid catastrophe akin to a nuclear accident or collective poisoning.
All the secrets hitherto safeguarded (sensitive data, encryption keys)—thanks to the impossibility of classical computers decomposing large prime numbers into prime factors—will be revealed by the quantum computer.
How Does the Multicoding Processor Work?
Over the past several decades, multitasking compilers have been made possible. Today, it is quite common to listen to music while writing a document, while also putting someone on hold who is trying to videoconference. This is possible thanks to binary calculation and the compilation power of the latest microprocessors.
Unfortunately, on the security side, this can become complicated. Indeed, Shor’s theorem has already sounded the alarm.23 All the secrets hitherto safeguarded (sensitive data, encryption keys)—thanks to the impossibility of classical computers decomposing large prime numbers into prime factors—will be revealed by the quantum computer. This is worrisome considering the security measures used to protect large quantities of sensitive information (e.g., medical data, banking data, classified government data) are dependent on the inability of conventional computers to break the keys designed, for example, by the RSA algorithm. Humanity would be in grave peril if a country, or even a single person, managed to break the keys that protect these information systems. Therefore, an intermediate system capable of protecting current systems from the quantum threat is needed; the proposed solution is a classic multicode compiler.
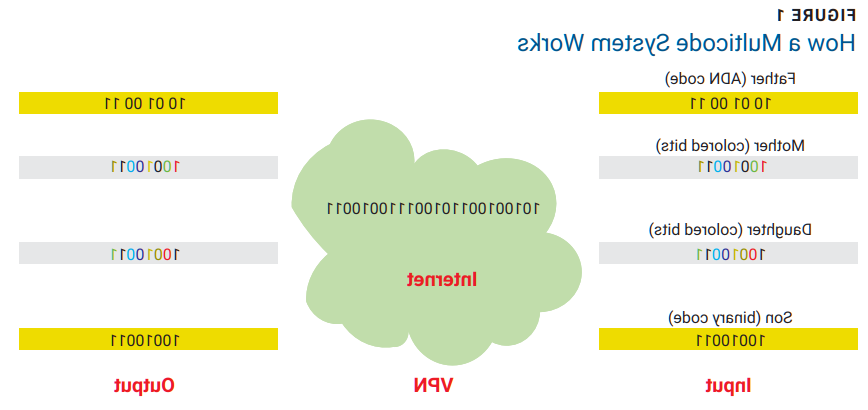
The functioning of this compiler is intimately linked to the hypothesis that it is now possible to design information systems with limited compatibility.24 This multicode compiler would use traditional bits (0 and 1), but unlike current compilers, it would be possible to encode the bits according to any numbering system (e.g., traditional Boolean calculation, colored bits taking frequency emission into account, bits from storage on synthetic DNA). Imagine a family of four. The father and mother are civil/public employees, the daughter is studying at university, and the son plays a video game. They use the same virtual private network (VPN) to connect to their respective sites. When connecting to his office, the father uses four bits (stored on DNA) to encode communications. The mother, during the same period, uses colored bits to make transactions with her bank. The daughter also uses colored bits to submit work to her university, while the son uses the Boolean calculation to connect to his video game site.
Advances in mathematics, photonics, synthetic DNA coding, 5G, and AI are positioned to be key players in efforts to rethink cybernetics.
As shown in figure 1, the coding system is different for each user, despite all of them being connected to the same network. The coding is being done, of course, without their knowledge (the fourth hypothesis). It is the machines at each end of the network that determine the communication coding system every hour, minute, second, and millisecond (fourth hypothesis). A man-in-the-middle (MiTM) attacker attempting to crack the encryption keys accompanying these communications would fail because nothing would be visible except a sequence of monochrome zeroes and ones. In addition, this compiler would take into account all the application layer encryption algorithms used so far, such as the RSA algorithm. Finally, the compiler would be able to process programs designed according to the latest algorithms working against the quantum threat unveiled by the US National Institute of Standards and Technology (NIST).25
Conclusion
There are numerous measures that can be implemented to improve the development of machines by fixing the flaws of the past. It is entirely possible to use the potential of the present to improve the future. Therefore, the creation of a theoretical information system has been presented.
Advances in mathematics, photonics, synthetic DNA coding, 5G, and AI are positioned to be key players in efforts to rethink cybernetics. If used wisely, they could help confront the quantum threat, the theft of personal information, and counterfeiting. But this journey must start today, or any attempt at remediation will be in vain. The most pressing challenge will be to put knowledge and safety before profit. In fact, some of the proposed applications already exist in an embryonic state. Others, like the colored bit design, have not yet materialized. One day, it will be necessary to process these different types of coding by a single processor in the same computer to increase data security.
Endnotes
1 FREENVESTING, “Warren Buffett: Why You Should NEVER Invest in Bitcoin,” YouTube, 1 December 2021, http://www.youtube.com/watch?v=XUsgoPAes8w&ab_channel=FREENVESTING
2 CBC News: The National, “He Helped Create AI. Now He’s Worried It Will Destroy Us,” YouTube, 10 May 2023, http://www.youtube.com/watch?v=CkTUgOOa3n8&ab_channel=CBCNews%3ATheNational
3 NBC News, “Hospital Ransomware Attacks Putting Patients at Risk,” YouTube, 2 November 2022, http://www.youtube.com/watch?v=PqBpSKTC0ak&ab_channel=NBCNews
4 Raphael, J. J.; Célestin, J. C.; et al.; “Chaos to the Rescue,” ISACA® Journal, vol. 4, 7 August 2019, http://i57d.images-collector.com/archives; Raphael, J.J.; Celestin, J. C.; et al.; “Against the Quantum Threat: Selective Compatibility,” ISACA Journal, vol. 5, 2022, http://i57d.images-collector.com/archives
5 Norwegian University of Science and Technology, “What Is Cybernetics?,” http://www.ntnu.edu/itk/what-is
6 Dictionary of the French Academy, “Cybernetics,” http://www.dictionnaire-academie.fr/article/A9C5393
7 Dico en Ligne Le Robert, “Cybernetics,” http://dictionnaire.lerobert.com/definition/cybernetique
8 Interstices, “How Does a Turing Machine Work?” 22 March 2013, http://interstices.info/comment-fonctionne-une-machine-de-turing/
9 Ibid.
10 Marinho, R.; “The First Calculator an Amazing Innovation,” Medium, 2 January 2022, http://regia-marinho.medium.com/the-firstcalculator-an-amazing-innovation-3e76ac883284
11 Computer History Museum (CHM), “The Babbage Difference Engine #2 at CHM,” YouTube, 2016, http://www.youtube.com/watch?v=be1EM3gQkAY&ab_channel=ComputerHistoryMuseum
12 Jaroeducation, “What Is Von Neumann Architecture and Its Impact on Modern Computing?,” Medium, 26 July 2023, http://medium.com/@jaroeducationnew2023/what-is-von-neumann-architecture-and-its-impacton-modern-computing-d70a21efd8a1
13 Shaw, K.; “The 7 Layers of the OSI Model,” Reseaux Telecoms, 26 October 2020, http://www.reseaux-telecoms.net/actualites/lire-les-7-couches-du-modele-osi-28083.html
14 Ibid.
15 Op cit Raphael et al., 2022
16 Merriam-Webster, “Achilles’ Heel,” http://www.merriam-webster.com/dictionary/Achilles%27%20heel
17 Fruhlinger, J.; “WannaCry Explained: A Perfect Ransomware Storm,” CSO, 24 August 2022, http://www.csoonline.com/article/563017/wannacry-explained-a-perfect-ransomware-storm.html
18 Lapirot, O.; “Why Do We Use 0s and 1s in Computer Language?,” 01net, 9 July 2009, http://www.01net.com/actualites/pourquoi-en-langage-informatique-on-utilisedes-0-et-des-1-504619.html
19 France 24, “Storing Our Digital Data on DNA,” 4 February 2022, http://www.youtube.com/watch?v=3HqSfIZe5xo; Slice Peuples, “DNA, a Storage Medium for ‘Big Data’?,” 5 March 2021, http://www.youtube.com/watch?v=Ev0Z7d3f4UY
20 Op cit Raphael et al., 2022
21 PhRMA, “Global Counterfeit Drug Threat; How Fake Medicines Threaten Consumers,” 11 March 2021, http://www.youtube.com/watch?v=IEWlpW9KFcM; VICE News, “Dangers of Illicit Medicines,” 12 September 2022, http://www.youtube.com/watch?v=C1GbfaxCkvo; VICE News, “The $500 Billion/Year World of Counterfeits,” 23 July 2021, http://www.youtube.com/watch?v=31AOa426Qi0
22 Kabir, M. S. A.; “Lessons Learned From the Bangladesh Bank Heist,” ISACA Journal, vol. 6, 2023, http://i57d.images-collector.com/archives
23 MinutePhysics, “How Quantum Computers Break Encryption: Shor’s Algorithm Explained,” YouTube, 1 May 2019, http://www.youtube.com/watch?v=lvTqbM5Dq4Q&ab_channel=minutephysics
24 Op cit Raphael et al., 2022
25 Perlner, R.; D. Cooper; Quantum Resistant Public Key Cryptography: A Survey, National Institute of Standards and Technology, USA, 14 April 2009, http://csrc.nist.gov/pubs/conference/2009/04/14/quantum-resistant-public-key-cryptography-a-survey/final
JEAN FAYOT
Is a researcher of cybernetics.
CLAUDE A. LABORDE
Is the former principal at Ecole Professionnelle Méthodiste de Frères, Haiti. He can be reached at info@simulninnov.com.
JEAN CLAUDE CÉLESTIN
Manages practical work at University of Ottawa (Ontario, Canada). He can be reached at jcele091@uottawa.ca.
